Accessing an AWS Account
Web GUI
The AWS services can be accessed by logging in to the web GUI, called AWS Management Console.
We use an access portal provided by AWS IAM Identity Center at: aws.sikt.no
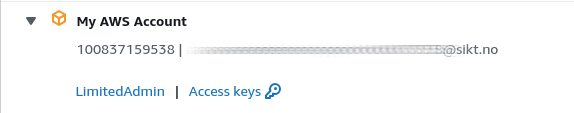
The portal will list the accounts you have access to.
Select an account for login, followed by choosing the appropriate role. For instance, in the following example, you would first choose My AWS Account, and subsequently select the LimitedAdmin role.
Custom colors
The AWS Management Console has multi-account support, so it is possible to be logged in to several accounts at a time.
To separate these, for example if you have a development/sandbox and a production account, you can set different colors at the top.
To set the color for an account:
- click the account name at the top right corner of the AWS console page
- click Account
- choose a color in the Account display settings
- click Update to save your selection
Platon strongly recommends choosing a red color for production accounts, and reserving this color to production accounts only.
CLI access
Installing the CLI
Install the latest version by following the install instuctions in the AWS CLI User Guide.
We recommend the latest version, but you need to have at least v2.9 or higher.
After completing the instructions, you should have an aws command.
First time instructions
Create a generic session setup for connecting to Sikt's AWS access portal, using the command
aws configure sso-session
You need to specify a session name. This name is used for configuring access to accounts later, so we suggest "sikt".
The start URL is: https://d-c3670fd13e.awsapps.com/start
The region is: eu-north-1
Accept the default registration scopes by pressing [Enter].
Example:
# aws configure sso-session
SSO session name: sikt
SSO start URL [None]: https://d-c3670fd13e.awsapps.com/start
SSO region [None]: eu-north-1
SSO registration scopes [sso:account:access]:
Completed configuring SSO session: sikt
Create a profile for an account
Start by issuing:
aws configure sso
-
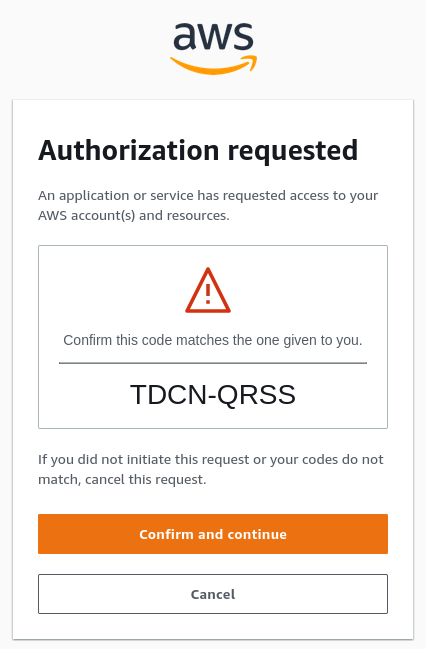
The CLI will ask for a session name. Use the name you entered above. The CLI will reuse the settings from that session definition and try to launch your browser:
-
If launching a browser fails, or you're running the AWS CLI remote on a server with no browser and no X11 forwarding, you can copy the URL and enter the code shown:
$ aws configure sso
SSO session name (Recommended): sikt
Attempting to automatically open the SSO authorization page in your default browser.
If the browser does not open or you wish to use a different device to authorize this request, open the following URL:
https://device.sso.eu-north-1.amazonaws.com/
Then enter the code:
GMSC-WDBL
- You will be redirected to Microsoft for authentication if necessary.
Then follow the instructions to allow your AWS CLI to access the AWS account:


After allowing access, the CLI will continue:
- If you have access to several accounts, you will be given a CLI menu listing them. Choose the account you want to access.
- If you have access to more than one role in this account, you get a CLI menu again with the roles you have access to. Choose the role you want.
- Then enter the default region you will be working in, ususally
eu-north-1oreu-west-1. - Enter the output format you want the CLI to produce output in (default: json).
- If the environment variable AWS_PROFILE was not set before you started the CLI, you can now type a profile name to save these settings into.
Example:
There are 2 AWS accounts available to you.
Using the account ID 087521752123
The only role available to you is: LimitedAdmin
Using the role name "LimitedAdmin"
CLI default client Region [None]: eu-north-1
CLI default output format [None]: json
CLI profile name [LimitedAdmin-087521752123]: default
To use this profile, specify the profile name using --profile, as shown:
aws s3 ls --profile default
You are now authenticated, credentials are stored in the file ~/.aws/credentials.
The credentials will last for 8 hours.
To reauthenticate, follow the instructions below.
Reauthenticate to an account
Pro tip: Set the environment variable AWS_PROFILE to the profile you want to use when working with the AWS services. Then you won't have to specify the --profile parameter to any command, not even the login command.
This is also very convenient if you need to work with several accounts at the same time. Use a separate terminal window for each account, with individual AWS_PROFILE values.
Use this command:
aws sso login --profile <profilename>
(You can omit the --profile parameter if you set AWS_PROFILE, as mentioned above)
Example:
$ aws sso login --profile default
Attempting to automatically open the SSO authorization page in your default browser.
If the browser does not open or you wish to use a different device to authorize this request, open the following URL:
https://device.sso.eu-north-1.amazonaws.com/
Then enter the code:
QFFD-CXWH
Successfully logged into Start URL: https://d-c3670fd13e.awsapps.com/start
Look up your identity
If you want to know what identity and account your are logged in to:
aws sts get-caller-identity
Example:
$ aws sts get-caller-identity
{
"UserId": "AROAYGDRDXTORZANK6KCH:fornavn.etternavn@sikt.no",
"Account": "087521752123",
"Arn": "arn:aws:sts::087521752123:assumed-role/AWSReservedSSO_<role>_<hexnumber>/fornavn.etternavn@sikt.no"
}