Dependency Track
Dependency-Track is an intelligent Component Analysis platform that allows organizations to identify and reduce risk in the software supply chain. It consumes, analyzes, and produces CycloneDX Software Bill of Materials (SBOM), an OWASP and industry standard.
Dependency Track is available at dependencytrack.sikt.no.
Platon has held an Office Hour about Dependency Track, with the recording available here.
Dependency Analysis
Dependency Track enables users to perform comprehensive dependency analysis on software projects to identify all direct and transitive dependencies. This includes libraries, frameworks, and components used by the project, along with their versions and metadata.
-
Dependency Discovery: Dependency Track automatically discovers dependencies by analyzing project manifests, such as package managers (e.g., npm, Maven, NuGet) and source code repositories (e.g., GitHub, GitLab).
-
Dependency Visualization: Dependency Track provides visualizations to represent dependency relationships, allowing users to understand the composition of their projects and the impact of dependencies on security. You can find the visualisation in Dependency Graph tab in each project.
Vulnerability Management
Dependency Track offers robust vulnerability management capabilities to identify and prioritize security vulnerabilities in dependencies.
-
Vulnerability Detection: Dependency Track continuously monitors known vulnerabilities in open-source components by integrating with various vulnerability databases and feeds, such as the National Vulnerability Database (NVD) and the Common Vulnerability and Exposures (CVE) database.
-
Vulnerability Scoring: Dependency Track assigns severity scores to vulnerabilities based on industry-standard metrics, such as CVSS (Common Vulnerability Scoring System), enabling users to prioritize remediation efforts effectively.
-
Vulnerability Intelligence: Dependency Track provides detailed information about vulnerabilities, including descriptions, affected versions, fix recommendations, and references to additional resources, to help users understand and mitigate risks.
How to Access
-
Login to dependencytrack.sikt.no using the Azure AD button
-
You should land on dashboard showing overview and status of your projects.
Dependency Scanning
SBOM can be generated by a list of tools like Trivy, Cdxgen, Syft and others. Dependency Track requires SBOM to be in cyclonedx format so any tool fulfilling this requirement can be used. Platon uses Trivy to generate SBOM when performing repository scan and in imagescan pipeline job. When SBOM is uploaded to a project in Dependency Track it overwrites the previous SBOM stored in Dependency Track.
-
repository: The list of dependencies (software bill of materials e.g. sbom) is created for each repository in GitLab every 24 hours with Trivy. Trivy supports dependency analysis of major programming languages. If your project uses a very specific language, Trivy might non be able to create the sbom for it. The sbom made from repository does not contain dependencies from image build (if the repository builds image).
-
special cases: If you work with the language not supported by Trivy consider using alternative tool: cdxgen. To upload SBOM to Dependency Track run the following script in your pipeline:
- export DT_PROJECT_UUID=$(curl -s -X "GET" "https://api.platon.sikt.no/v1/gitlab/project/${CI_PROJECT_ID}/dt-id" | jq -r ".dt_id")
# export image to Dependency Track
- |
curl -s -X "POST" "https://dependencytrack.sikt.no/api/v1/bom" \
-H "Content-Type: multipart/form-data" \
-H "X-API-Key: ${DT_PLATON_AUTOMATION_API_KEY}" \
-F "project=${DT_PROJECT_UUID}" \
-F "bom=@./sbom.json"where:
CI_PROJECT_IDis your GitLab project ID. The project id variable will be replaced automatically by the pipeline.DT_PLATON_AUTOMATION_API_KEYis a global variable available for all projects in GitLab.
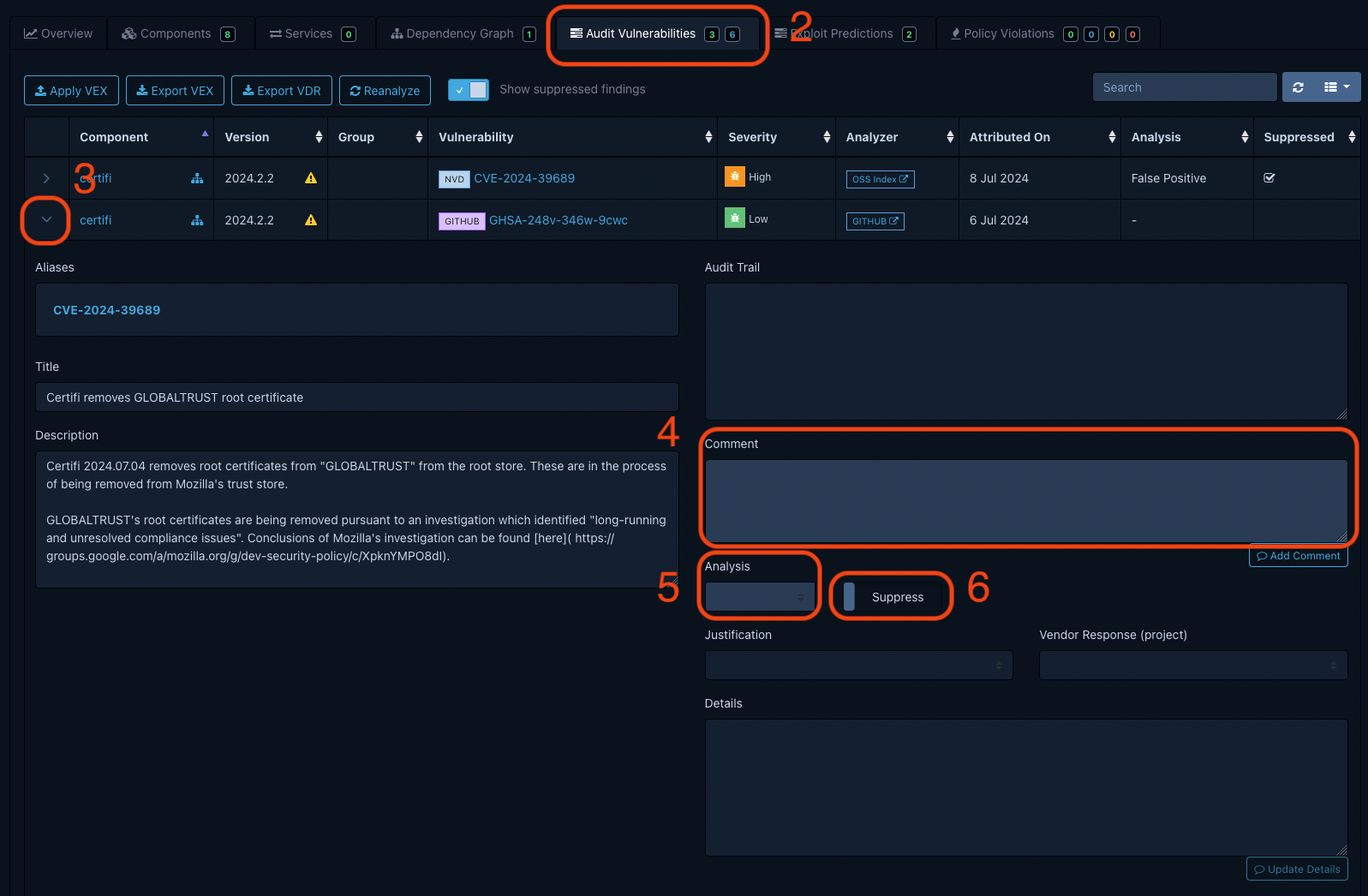
Hiding False Positives
While Dependency Track provides valuable insights into vulnerabilities, sometimes it may flag false positives. Users can suppress these false positive vulnerabilities to maintain a cleaner and more accurate vulnerability management environment.
To hide a false positive in Dependency Track, follow these steps:
- In Dependency Track, open the project you want to hide false positives in.
- Navigate to Audit Vulnerabilities
- Click the small arrow next to component containing the vulnerability you want to hide.
- Provide justification for suppressing the vulnerability in Comment.
- Choose the reason for suppressing the vulnerability in Analysis.
- Hide the vulnerability by sliding the Suppress button.
- Dependency Track will log all changes in the Action Trail window.
Notifications to Slack
Dependency Track can send notifications to Slack (or other messaging services) when new vulnerabilities are detected. Every developer with access to Dependency Track can create a new notification rule.
- If you want to be notified about new vulnerabilities in your projects, navigate to Administration panel on right side → Notifications → Alerts → Create Alert.
- Fill in the Name of the alert, keep default scope (Portfolio), select notification level and publisher.
- Click on the newly created alert to specify the receiver of the alert in Destination.
- Specify the Dependency Track project you want to monitor for new vulnerabilities. Click on Limit To and add the projects.
You can read more about notifications in the official documentation here.
Troubleshooting
If you have any questions, please contact us at our #platon Slack channel.
403 Error After Login
The access to Dependency track is configured with OIDC provider towards Azure AD. Each GitLab group should be tagged with Azure AD ID in description. The Azure AD ID is then synced to Dependency Track to map access control between teams and projects. If you get error when logging in, or you don't see any data on the dashboard after login check the following:
GitLab group you are associate with has Entra ID (formerly Azure AD ID) in description. If not, add it. There are 2 alternatives how to add Entra ID (formerly Azure AD) GitLab group:
- Go to over.sikt.no and find your group in the search bar. The group ID is located under the team's name.
- If you for some reason can't find the team in oversikt, go to myaccount.microsoft.com/groups and search for group which fits the GitLab group. The naming of groups is not universal across Sikt and therefore it is not possible for us in Platon to write the specific format. If you are in doubt consult with your leader/team. The group ID in the URL of that group.
Add the ID to your GitLab group description. The allowed formats are:
[PTID:<azure_ad_uuid>]- Product Team ID[PAID:<azure_ad_uuid>]- Product Area ID
There can also be case when you are owner of Azure AD group but not a member. You have to be member of a group in order to be associated with the right projects in Dependency Track.
You don't see all projects
You have access only to projects that are tagged with Azure AD ID group that you are member of. If you want to access project that is in group you are not member of, contact the group owner to include you to the desired group.